
When you store any data in your computer, it is stored in a human-readable form. Thus, if someone gets access to your computer, he/she can access the data stored in your computer even though you may have kept a password on your computer system’s account. All it takes is to plug in the hard-disk into another computer and access the contents of the hard-disk. If certain text is stored in human-readable form, it is called plain-text, i.e. stored as a plain text. If sensitive data like user-names, passwords, bank account details, etc are stored in plaintext, there is always the risk of them being compromised. This is where encryption comes in.
In the simplest of terms, encryption is a process by which a human-readable plaintext is converted into a form of text that is difficult to understand or not understandable by humans. This conversion is done by using a series of steps based on the input -> process -> output model. These series of steps that take an input text, process it and give out a form of text not understandable is called a “cipher”. Thus, a cipher converts a “plaintext” into “ciphertext”. Now, there are a variety of ciphers available, and each one of them will convert a given plaintext into a different ciphertext. This is because each of the ciphers process the plaintext in different ways and thus output different resultant ciphertext.
It is to be noted here that encryption is a type of cryptography, which is anything that involves secret communication. Also, conversion of the encrypted ciphertext back into plaintext is called decryption.
Now, a particular cipher may either give a fixed output for certain fixed input or it may allow the user to provide a key (a key is simply an auxiliary information) and thus give different output for different key values. This can be better understood with the following example.
Suppose there is a cipher that simply reverses the text that you provide to it. Thus every time that you input “hello”, it gives “olleh” as the output.
On the other hand, there is a cipher that rotates the character to the left in a text depending upon the key value you supply to it. For example, if you supply the key as 1, “hello” becomes “elloh” as every character is rotated by 1 place to the left.

Similarly, if you supply the key as 2, “hello” becomes “llohe” and so on.
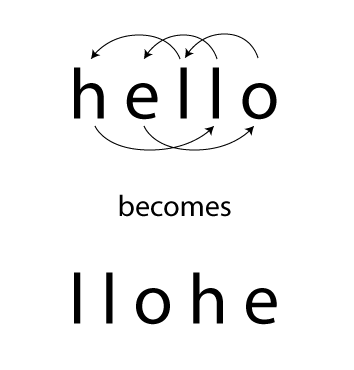
The above cipher examples are very rudimentary examples of ciphers and can easily be broken down by modern computers. The ciphers used for encryption in modern technology are very much complex as compared to the above examples.
The input data that is fed to a cipher can either be processed in chunks (or blocks) of data or it may be processed as a continuous stream of data. Based on this condition, ciphers are usually of 2 types:
- Block Ciphers – These ciphers take a data chunk of fixed size (for example 64 or 128 or 256 bits) and output corresponding ciphertext of same length. This fixed size is called block length. If the last chunk is of a smaller size than the block size, the input is padded with random data to match the block size and then a corresponding block is provided as output. Some of the popular block ciphers are DES, 3DES, AES and Blowfish.
- Stream Ciphers – These ciphers process the data one digit (or bit) at a time and a corresponding output is produced for each digit (or bit). RC4 is a popular stream ciphers.
A mention needs to be made of the “key” that we talked about, if the key length is more, the cipher is generally considered to be more secure than a cipher with a smaller key-length since guessing they key length or finding it out computationally will be more time taking and will need more resources.
Another categorization of encryption can be as follows:
- Symmetric Key Encryption: Here, the same key that is used for encryption is used for decryption by retracing the steps back. For example as mentioned above, rotating left by using a key 1, “hello” becomes “elloh”. In decryption, the reverse is done, i.e. rotating right. Thus “elloh” becomes “hello” by rotating one character to the right. Thus, same key is used for both encryption and decryption process.
- Asymmetric Key Encryption: In this method, two mathematically compatible keys are generated in such a way that one key is used for encryption and the other key is used for decryption. Thus, text encrypted with one key can be decrypted with the other key and vice-versa. This is also called as Public Key Encryption or Public Key Cryptography. To read more about it, click here.
Any attempt to break an encryption algorithm must use some form of “cryptanalysis” which is the process of finding out some flaw in the cipher or obtaining details or pattern about the cipher from the relation between the plaintext and ciphertext.
For Wikipedia entry on Encryption, click here.
For more posts on Cybersecurity, click here.
For more posts in The Cyber Cops project, click here.
